-26%
Ubel Android Banking Botnet (Latest)
Original price was: $299.00.$220.00Current price is: $220.00.
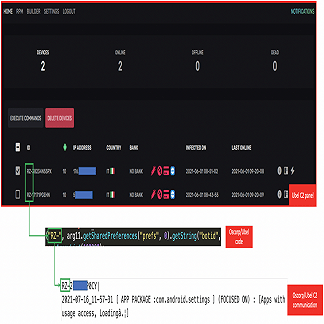
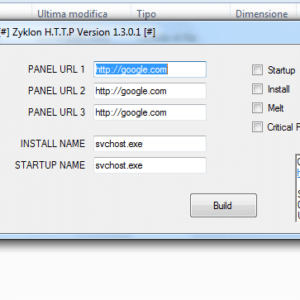
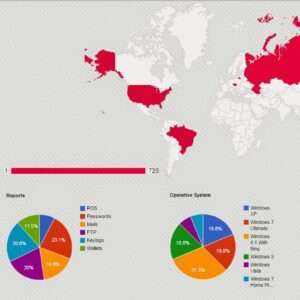
Ubel Android Banking Botnet The malware was distributed through malicious SMS messages, with the attacks often conducted in real-time by posing as bank operators to dupe targets over the phone and surreptitiously gain access to the infected device via WebRTC protocol and ultimately conduct unauthorized bank transfers. While no new activities were reported since then, it appears that Oscorp may have staged a return after a temporary hiatus in the form of an Android botnet known as UBEL.














Reviews
There are no reviews yet.